Two weeks of DNS Dampening
The first two weeks of counter-measurements to DNS amplification or reflector attacks are over. The server did not send out attacks anymore and therefore became significantly less attractive to the attackers. A great success story.
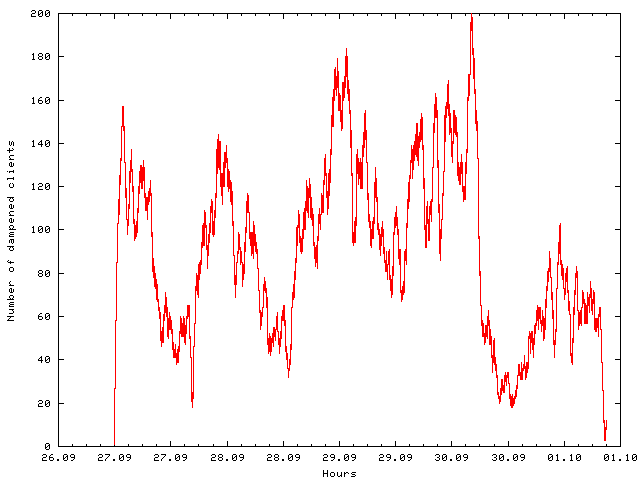
The system is running since days without interruption. Time for publishing new statistics.
Variations in numbers of catched clients follow a daily pattern. Attackers tend to prefer a common time zone. Which one? I don't know, I'll not even try to guess.
But the more remarkable fact is the sudden decrease of attackers. It looks like a coordinated behavior, like publishing a new list of possible amplifying reflectors each weekend. I did see those sharp increase and decrease of attack volume since several weeks. If somebody knows how to search the relevant pastebins and can retrieve such lists there, please drop me a note.
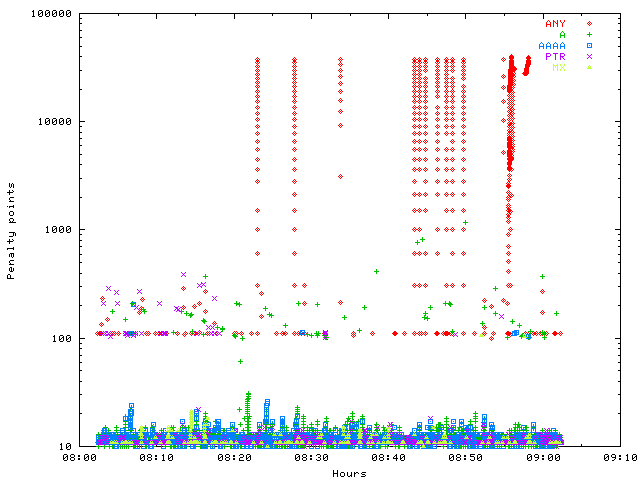
But back to the interesting data. Which query types are the usual suspects?
Of course ANY. And each of those attacks still follows the same dumb pattern: Send out ANY queries with the same ID as fast as possible. Within seconds, the penalty reaches the limit and my participation in the attack is stopped. Real world queries remain unaffected:
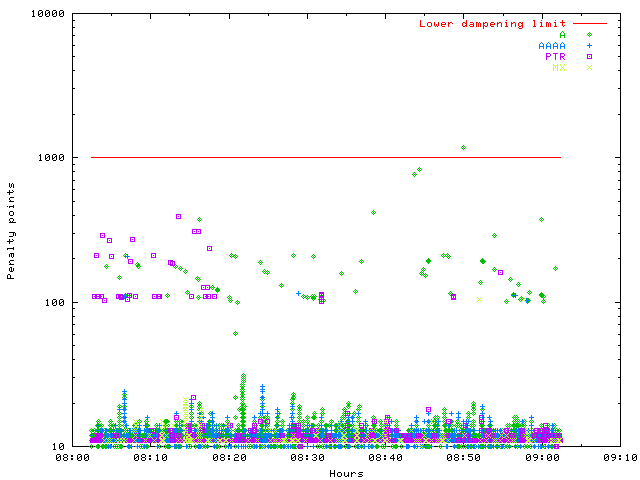
Even here ANY queries occur (visible by the 100 point increase), they are part of the normal DNS traffic and must be respond. Most probably a qmail MTA is trying to send a legitimate email. Between 8:35 up to 8:50, a single clients sends out many ANY queries (interspersed by A queries which are show in the diagram). That's not an attack! But non of those clients went into dampening, they all got their answers.
Looking at the daily incoming traffic of the server reveals a promising result: The incoming attack bandwidth dropped from ten Mbps to below two Mbps within two weeks. This server becomes less attractive to the attackers and therefore drops from their lists. A great achievement!
In principle DNS dampening fulfills my needs: Now it's time to carefully create a real useful patch and compare it to other methods.

Total 2 comments